Enhance IT and security operations with an automated endpoint and vulnerability management platform. Focus on your business instead of worrying about IT and cyber risks. Gain visibility and control over your infrastructure, with real-time alerts, risk-based vulnerability prioritization, and an intuitive orchestration engine to ensure effortless operations.

Syxsense Secure provides enterprises unified endpoint management with a powerful no-code automation to deliver a robust, cloud-native solution that supports all your IT management and compliance needs.
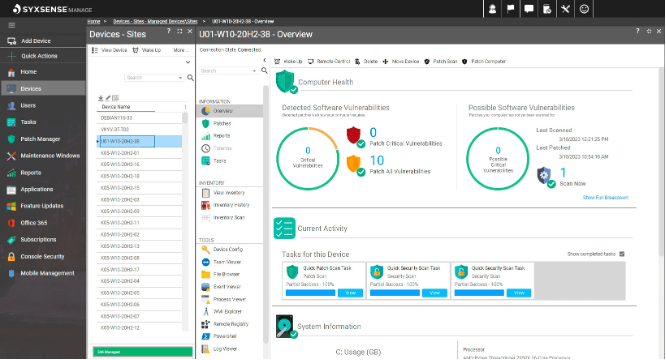
Automate and streamline the patch management process to reduce the risk of security breaches and system downtime caused by software vulnerabilities.
Manage. Scan. Deploy.
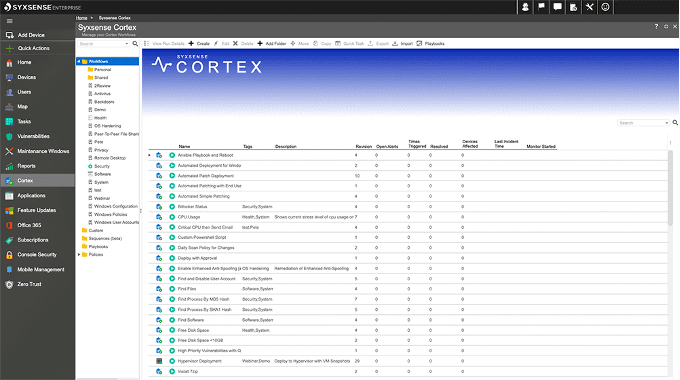
Syxsense Cortex, a unique automation and orchestration engine, enables IT Operations and Security Operations teams to actually do more with less.
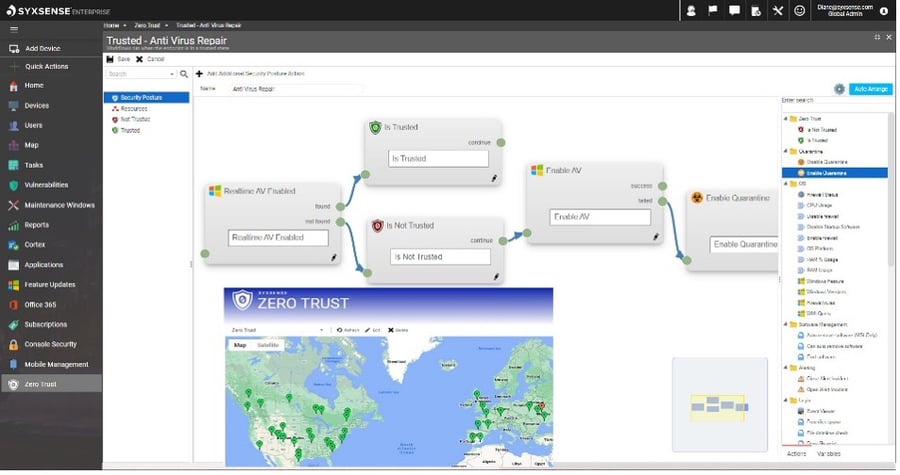
Syxsense makes implementing a Zero Trust endpoint strategy easier and customized to your organizational policies. Informed by a cause-and-effect, policy-based evaluation, enterprises can have continuous Zero Trust device attestation for enhanced cybersecurity.
With our unified endpoint and vulnerability management platform, customers can manage their critical IT infrastructure, scan and remediate vulnerabilities, and report on IT, security, and compliance requirements easily. Instead of having to jump from tool to tool, everything can be accessed from a single console, lowering your total cost of ownership.
Every customer receives award-winning onboarding, training, and support. Our implementation process is grounded in each customer’s unique strategic objectives, and this provides the roadmap for our custom onboarding. Our goal is to meet each customer’s key objective within 30 days of the start of onboarding to ensure they are getting the most value as quickly as possible.
Syxsense customers can easily achieve, maintain, and prove compliance for a variety of regulatory requirements, such as HIPAA, SOX, and PCI DSS, and security frameworks, such as CIS Benchmarks. Our in-depth reporting minimizes the burden of documenting and demonstrating compliance in audits and in meeting many security requirements required for cyber insurance.
Accurately identify, prioritize, and remediate IT and cyber risks based on your enterprise’s infrastructure and assets. With our Syxscore, you get a risk score that leverages details from the National Institute of Standards and Technology (NIST) and the Common Vulnerability Scoring System (CVSS) as well as vendor severity assessments in relation to the status and number of endpoints in your environment. With a clearer view of your organization’s attack surface and the security posture of your endpoints, your IT operations and security teams can focus their time and energy on securing your enterprise.
You can have a private, secure console up and running with your own live device data in under five minutes. Our lightweight and responsive micro-agent is ready to deploy to every device in your enterprise, with support for Windows, Mac, Linux, iOS, and Android operating systems.
Understand current practices, obstacles, and perspectives in vulnerability management. In conjunction with Cybersecurity Insiders, this report of findings offers strategic insights and industry benchmarks.
Syxsense has been named an Outperformer and a Leader in the GigaOm Radar Report for Patch Management. IT organizations can use this report as a guide to assessing competing solutions based on well-defined features and criteria, and it provides a forward-looking analysis of vendor solutions along multiple axes based on strategy and execution.
VLCM enhances EPB of Chattanooga's cybersecurity with Syxsense, streamlining patch management, improving efficiency, and fortifying IT infrastructure.
After years of inconsistent service with other services and solutions, while
facing increasingly urgent security threats, EECO sought a single endpoint
management and security solution that would enable them to improve
support to their distributed employees across several states and face the
challenge of remediating critical vulnerabilities such as Follina.
Take a step further to strengthen your security posture. Get started today. Submit the following form to get in touch with a VLCM representative within 1-2 business days.